The MigratoryData server ensures security through various measures, including:
- Employing TLS/SSL, which is a widely-accepted industry standard for encrypting communication with clients
- Implementing TLS/SSL encryption and authentication for JMX, HTTP, and Prometheus monitoring
- Offering a configurable list of TLS/SSL ciphers
- Enabling password protection for inter-cluster communication
- Configuring the server to run as a non-privileged user
- Supporting dual firewall and DMZ policies for deployment
- Allowing message publication only from a configurable list of IP addresses
- Implementing authorization for data access protection
Example of dual-firewall DMZ deployment
Usually, MigratoryData is set up to receive client connections from the internet by means of TLS/SSL encrypted
connections on a public IP address, utilizing the default TLS/SSL port 443. It is important to note that only one port
443 is necessary to accommodate millions of client connections.
While not mandatory, for backend clients, MigratoryData can be set up to use a private IP address as in the following example of a dual-firewall DMZ deployment:
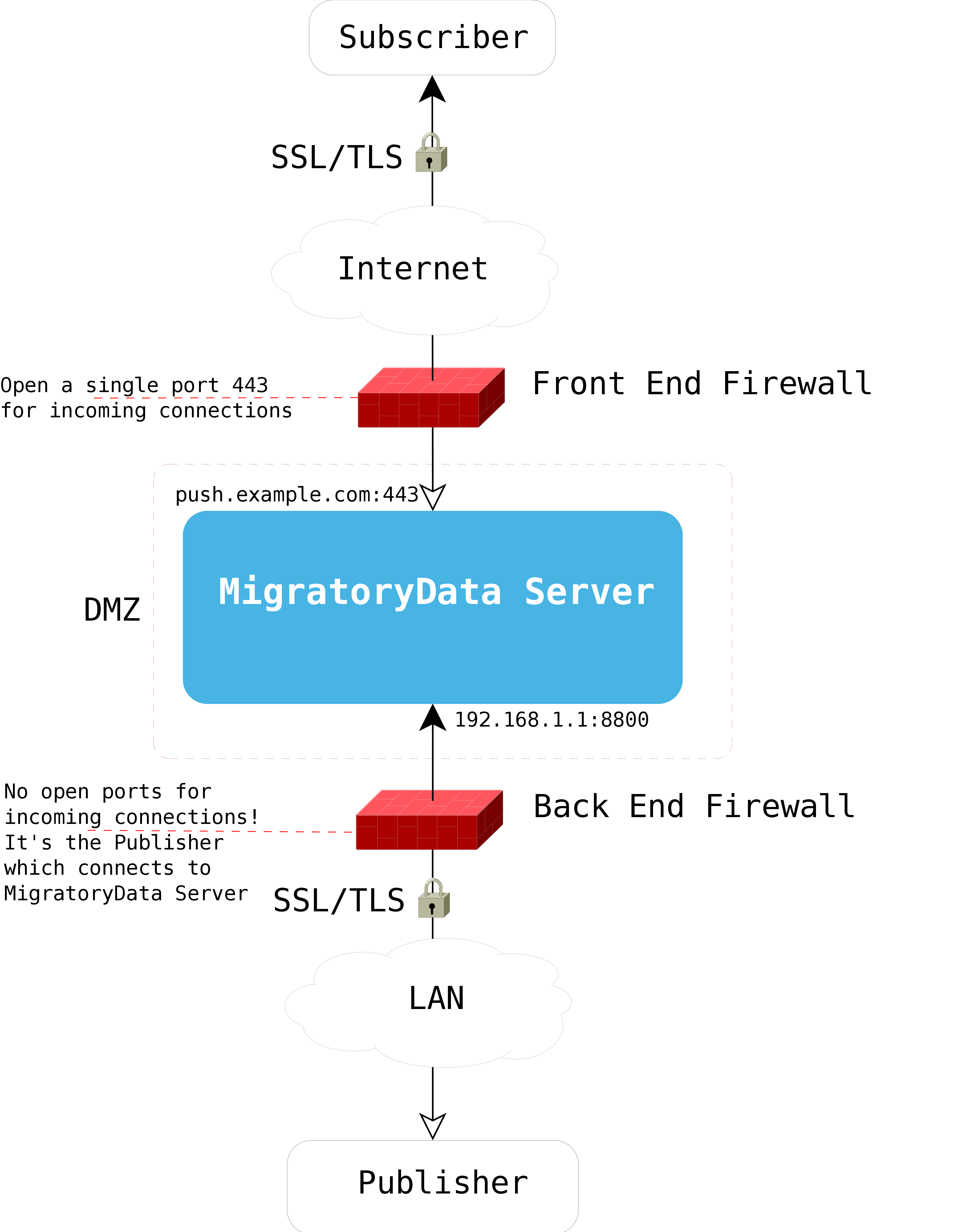
Note that there is no need to open any port for incoming connections on the back end firewall. It is the client that establishes a connection to the MigratoryData server.
Authorization
The goal of authorization is to provide a mechanism of data control that ensures that clients can only access messages related to the subjects they are authorized to subscribe to and can only publish messages for the subjects they are authorized to publish on.
Currently, there are four types of authorization methods as defined by the parameter Entitlement of the MigratoryData server:
None
This method allows any client to subscribe to and publish on any subject.
Basic
With this method, all clients are permitted to subscribe to any subject. However, publishing messages is only
permitted from clients that have been authenticated with an entitlement token specified by the
EntitlementAllowToken parameter of the
MigratoryData server. To assign an entitlement token to a client, the client API offers a method called
setEntitlementToken().
JWT
This method allows clients to subscribe and publish based on JWT tokens using the JWT Auth extension. Please refer to the documentation of this extension to learn how to use this auth method.
Custom
With this method, you have the ability to define custom entitlement rules. By utilizing the Extension API, you can create an extension for the MigratoryData server that implements your specific entitlement rules. This will allow you to authorize clients to subscribe to or publish messages on particular subjects according to your own specifications.
